California introduces proposal to expand data breach notification law
Passport numbers and biometric data are not currently required by law to be reported breached
In brief: California is introducing new legislation that expands on current data breach notification requirements. The state’s attorney general announced the proposal yesterday. It looks to add passports and biometric data to the list of “personal information” that is protected under current California law.
California is introducing new legislation that expands on current data breach notification requirements. State Attorney General Xavier Becerra announced the proposed bill on Thursday.
Drafted by Becerra an Assemblyman Marc Levine, the law will require companies to notify customers if their biometric data or passport numbers have been compromised. Existing legislation passed in 2003 only holds health insurance information, medical data, credit card, driver’s license, and social security card numbers as being “personal information.”
Becerra says the bill would expand the current protections. The proposal was prompted by the Marriott/Starwood breach last November in which hackers stole over 500 million customer records including 25 million passport numbers.
AB 1130 will increase our efforts to protect consumers from fraud and affirms our commitment to demand the strongest consumer protections in the nation.
“Knowledge is power, and all Californians deserve the power to take action if their passport numbers or biometric data have been accessed without authorization,” said the California AG. “We are grateful to Assemblymember Levine for introducing this bill to improve our state’s data breach notification law and better protect the personal data of California consumers. AB 1130 closes a gap in California law and ensures that our state remains the nation’s leader in data privacy and protection.”
Becerra notes that while Marriott did notify customers of the Starwood breach as required by law, he is not so sure that would have been the case if it were only the 25 million passport numbers that went missing, which are not currently required to be reported.
Identity theft and fraud are on the rise with millions of records being sold on the dark web every day. With so many companies controlling consumers’ digital fingerprints, both figuratively and literally, lawmakers view the disclosure of breaches to that information of the most vital importance. The public must be allowed to know there are real or potential bad actors accessing their data so they can take immediate action.
By: Techspot
Chrome is only as secure as the extensions you use
With a market share north of 61 percent according to StatCounter, Google’s Chrome is far and away the most popular web browser out there. Odds are, you’re probably using it to read this right now and if I were a betting man, I’d wager that you also probably have some extensions installed.
Google has worked tirelessly to ensure a secure experience with Chrome but its safeguards don’t necessarily extend to extensions as one security firm has discovered.
Duo Labs recently announced the public beta of CRXcavator, a free service that analyzes and produces comprehensive security reports on Chrome extensions.
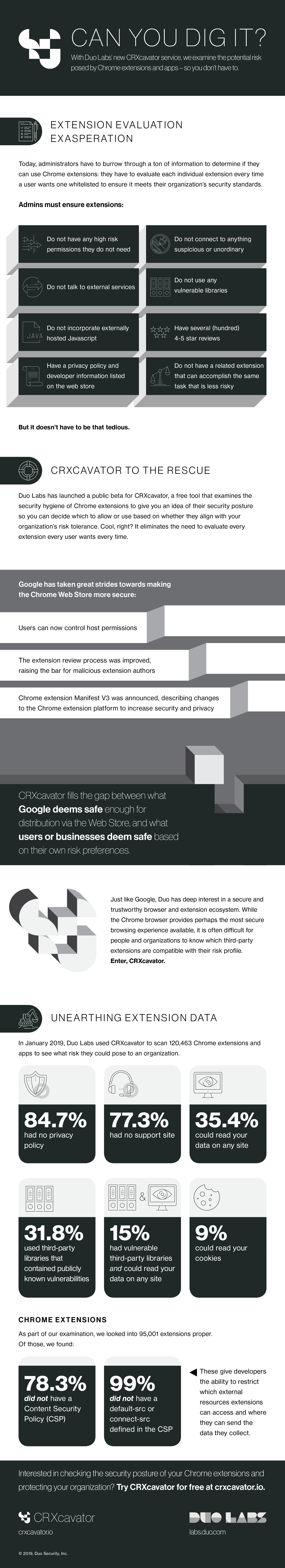
Curious as to the state of the ecosystem, Duo in January discovered and processed 120,463 extensions and apps using its new tool. Of those, 38,289 (31.8 percent) were found to be utilizing third-party libraries that contain publicly known vulnerabilities. More than a third of extensions (35.4 percent) can read your data on any site, Duo said.
Furthermore, the team found that 102,029 extensions (84.7 percent) do not have a privacy policy listed and 93,080 (77.3 percent) do not reference a support site.
By: Techspot
[/fusion_text][/fusion_builder_column][/fusion_builder_row][/fusion_builder_container]
Got a spare $43,000? You could spend it all on this monster PC
43 grand is, of course, an awful lot of money for a computer, but this isn’t your everyday PC. Designed by overclocking champion Ian “8Pack” Parry, the OrionX2 is actually two overclocked systems packed into one case, making it a workstation/gaming machine combo.
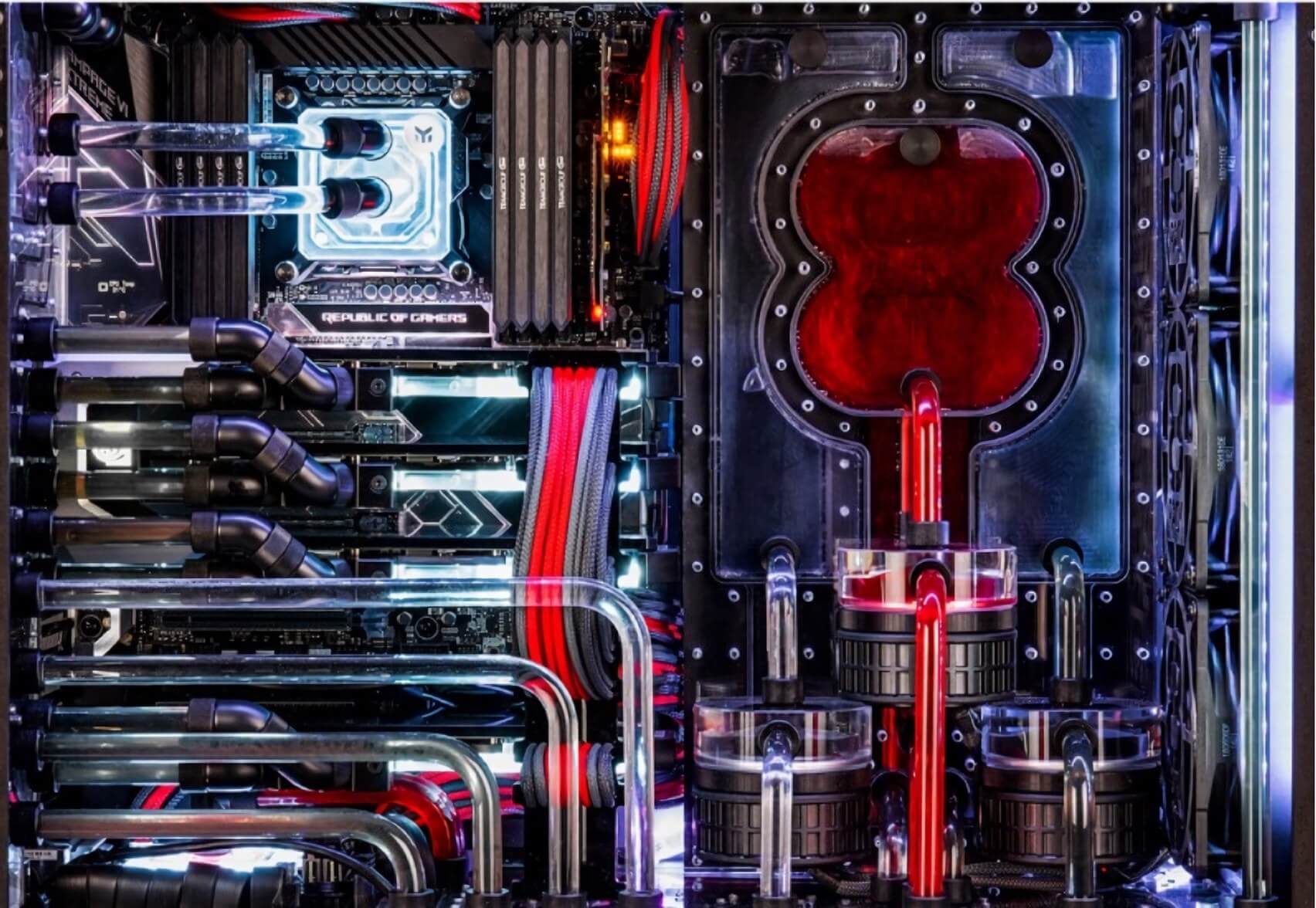
The primary system is comprised of an ASUS Rampage VI Extreme Omega Edition E-ATX motherboard and an 18 core/ 36 thread Intel Core i9-7980XE processor overclocked to a minimum of 4.6GHz.

Graphics are provided by the world’s most powerful desktop GPU: the $2,499 Titan RTX. Buyers can choose to have either three of them running independently or two of the cards connected by NV-Link. It also comes with 128GB of RAM clocked at 3200MHz, two 2TB Intel 970 Evo M.2 NVMe SSDs, and a 14TB Seagate Ironwolf Pro HDD.
Even the secondary system is the stuff of gamers’ dreams. It features an ASUS ROG Strix Z390I Gaming Mini-ITX motherboard and an Intel Core i7-9700K overclocked to 5.0GHz. There’s another Titan RTX card for some 4K gaming, along with 16GB of RAM, two more 2TB Samsung 970 Evo M.2 NVMe SSDs in RAID 0, and another 14TB Seagate Ironwolf Pro HDD.
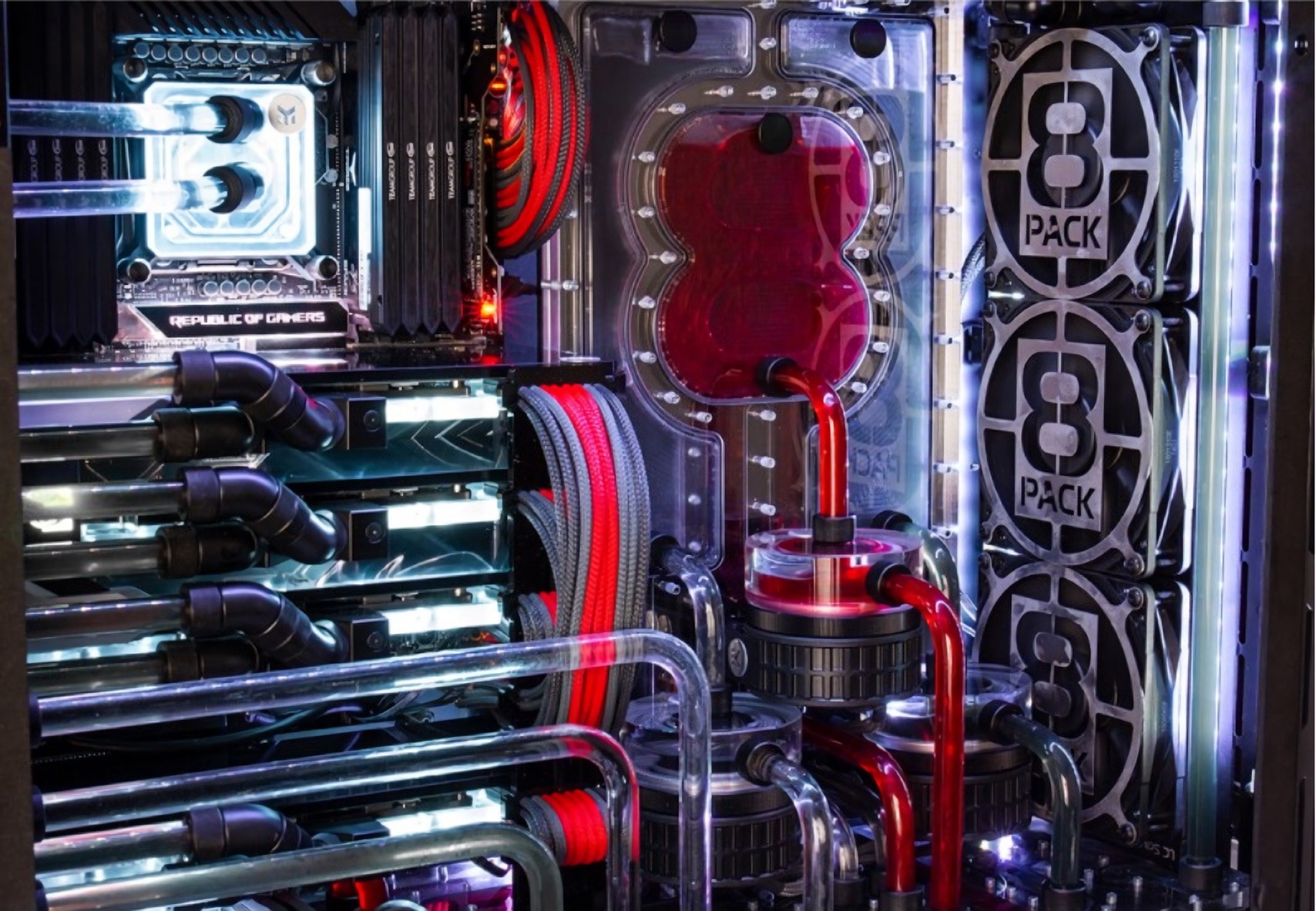
With all those high-end components receiving the 8Pack overclocking treatment, a special liquid cooling system was required. It’s made up of three independent loops (with custom acrylic pass-through plates), seven reservoirs, three pumps, and 5 meters of hard piping. In total, the system contains 8 liters of coolant.
Everything is housed in a modified Phanteks Enthoo Elite case and powered by a 2000W PSU. All it needs now is pairing with some $2000 Asus or Acer 4K/HDR/144Hz G-Sync monitors.
By: Techspot
Apple is removing the Do Not Track setting from Safari
Back in 2010, the FTC proposed a browser setting, “Do Not Track,” so that advertisers would know not to collect a specific user’s information based on their personal preferences. After implementing such a feature in 2011, Apple is removing Do Not Track options from Safari on iOS and MacOS.
Compliance with the Do Not Track setting has always been suspect. It is completely up to website developers to comply with the request of anonymity being made. Just because a user has the setting checked off does not mean that advertisers are actually respecting their choice.
Clever methods of tracking users involve collecting all of the information a browser shares with a server and then creating a profile based upon the metadata gathered. This process is known as browser fingerprinting. Apple is removing the “Ask Websites Not to Track Me” option so that it is more difficult to differentiate between different MacOS and iOS users. In earlier versions of iOS, this is simply called “Do Not Track.” Any extra information makes it slightly easier to profile site visitors.
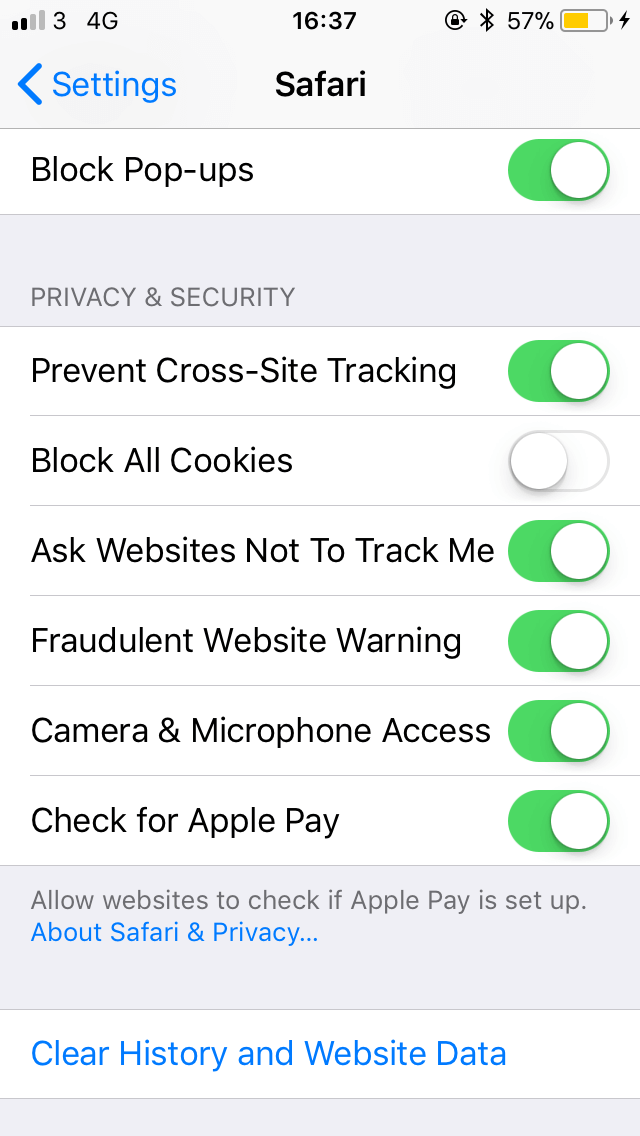
Beginning with iOS 12.2 and MacOS 10.14.4, Safari will no longer request that websites stop tracking you. Instead, Apple’s cross-site tracking prevention will act as the main method of blocking your personal information from being widely collected and distributed. This setting should already be enabled by default, but can be found under Safari’s privacy settings should you wish to verify.
As part of Safari 12, Apple has upgraded its tracking prevention tools, changing the name to Intelligent Tracking Prevention 2.0. Additional protections against cross-site script inclusion attacks and cross-site framing have been added.
Image Credit: PixieMe via Shutterstock
By: Techspot
Microsoft reveals how much Windows 7’s extended support will cost
Why it matters: We know that Windows 7 users now have under 12 months before Microsoft ends its extended support for the aging OS. After January 14, 2020, the only people who will receive extended security updates (ESUs) will be business and education customers willing to pay for them. Now, Microsoft has revealed how much that will be—and it’s not cheap.
Following the end of its extended support period, ESUs will be available to all Windows 7 Professional and Windows 7 Enterprise customers with volume licensing through January 2023. Microsoft is charging on a per-device basis, with Windows 7 Pro users paying more than Windows 7 Enterprise customers—the company aims to move more businesses onto the latter platform.
During the first year of ESUs (January 2020 to 2021), those using Windows 7 Enterprise will pay $25 per machine. This doubles to $50 in the second year and goes up to $100 for the third year.
Staying on Windows 7 Pro is going to cost even more. ESUs will start at $50 before going up to $100 in year two and $200 during year three.
Those prices mean that businesses with hundreds or thousands of Windows 7 devices can expect to hand over a lot of money. Microsoft will likely offer a discount on bulk purchases, though this has yet to be confirmed. Ultimately, however, the cost and effort for many companies will be less than upgrading their entire network to Windows 10.
Despite Windows 7 entering the last 12 months of extended support, more people started using the operating system last month. Windows 10 still holds the lead, but the older OS’ market share increased by 0.29 percent throughout January.
Image credit: g0d4ather via Shutterstock
By: Techspot
macOS Mojave contains a major flaw that can reveal passwords and encryption keys to attackers with physical access
In brief: Security researcher Linus Henze posted a video to his YouTube channel allegedly demonstrating a zero-day exploit he discovered in macOS Mojave, but he is not sharing details with Apple out of protest.
Keychain is a built-in password manager for macOS. It houses passwords, encryption keys, and certificates from a wide range of sources including websites, apps, and attached hardware. Using a software tool he created called “KeySteal,” Henze can access all the passwords on a Mac’s keychain with one click.
He says that the exploit is similar to Patrick Wardle’s 2017 “KeychainStealer,” but whereas Apple has patched that vulnerability, this one is still wide open. He says that the program works without administrative privileges or root passwords. It also works with macOS login and system keychains.
He tested it on a 2014 MacBook Pro, and it worked flawlessly. However, it’s unclear if the exploit can get past the security chips in newer MacBooks.
Typically, researchers do not reveal security flaws until the company has been notified and has had time to patch it. However, Henze said he is posting the vulnerability publicly because Apple has no bug bounty program for macOS. The company does have one for iOS, but it is so limited in scope, and difficult to get rewarded from it is almost useless. Just ask Grant Thompson, the boy who discovered the FaceTime bug.
Despite not disclosing the details to Apple, Henze says he will not reveal how the exploit is performed to anyone else either. He is not looking to harm Apple or its users, just to inform them of the problem. It is up to Apple to figure out what is wrong — at least until it starts a proper bug bounty program.
In the meantime, Henze will be posting other Apple product exploits that he discovers under the hashtag #OhBehaveApple.
“The reason is simple: Apple still has no bug bounty program (for macOS),” he explains. “Maybe this forces Apple to open [one] at some time.”
By: Techspot
 Toll Free: 888-88-CADAN
Toll Free: 888-88-CADAN Support
Support Client Login
Client Login